WordPress is one of the most popular CMS worldwide. Check out ManageWP's Blog post just to see how incredibly popular it is. 74.6 million sites depend on it. According to W3 Techs 23.4% of all websites use WordPress and TechCrunch mentions 22 out of 100 active domains in the US use WordPress. Quite a feat. This unfortunately also means it is a very interesting target for hackers. In this post Ten Quick WordPress Security Tips anyone can take to improve their WordPress Site's Security.
How are WordPress Sites hacked?
WordPress sites are hacked most of the time because of bad server configuration, second reason is bad themes and third reason is faulty plugins. Fourth reason is bad passwords. This according to data by Themasoup from 2010-2012. The same causes are mentioned by Smashing Magazine here and are also experienced by our clients.
Typical Attacks
Typical attacks are
- Backdoors (shell scripts),
- Drive-by downloads (often a payload on your user’s local machine),
- Pharma hacks (meta spam, page spam links),
- Malicious redirects.
I will do some more blogging on examples in the future, but do check out this excellent Smashing Magazine post in the meanwhile.
Hardening Solutions
I will start with two more obvious tips or tips that should be obvious and then I will move on to 3 that are less obvious and or require some changes on your server.
WordPress Security Tip I – Updates and Backups
One of the two most obvious things that needs taking care of are backups and updates. Like with any operating system or piece of software backups and updates are important. Unfortunately they are not alway taken care of properly.
Backup!
This might be evident for some, but in my experiences many bloggers and other users of WordPress do not backup or do not backup often enough.
Frankly a lot of clients are just too busy with their own business to update. Others simply think paying to get a a site up and running is all that is needed and they no longer pay attention to it. That is a bad idea.
Make sure you have local, external as well as copies on the live server. Just in case something goes wrong on the live server, a third location or God forbids your site gets hacked. Cleaning up a hacked WordPress site because there is not a recent or decent enough backup is a major headache and will cost you time and $. For backing I can highly recommend BackupBuddy and me to take care of it for you.
Update Your Site Often
Again something you can do and with ease, but still something that many end users simply do not do. Even though WordPress can auto update you still need to take care of the plugins. And you need to make sure WP updates go well. Even though auto updates work well 99% of the time or even closer to 100% in my experience you still need to double check AND update the plugins and themes by yourself.
Auto Updating Core OK, Not for Plugins
There are plugins – i.e. Advanced Automatic Updates – that help you auto update the plugins too as well as WordPress filters, but that is risky as most sites of clients run 20+ plugins and the chances something goes wrong are quite high because of this. I would say, keep WP Core updates turned on, but do plugins manually and check what changes entail before going ahead. Again I can do this for you as your WordPress Remote Webmaster 😉 .
WordPress Security Tip II – Server Access – Secure Setup
To make it harder for hackers into your computer you need a good server setup. If you are on a shared hosting environment that is largely up to the hosting provider, if you are on a VPS or dedicated server is mostly or all up to you. But in all cases there are things you can do.
SFTP and SSH
Use SFTP not FTP to upload and download files. FTP is not encrypted and therefore not secure. SSH from the commandline is a great tool too, but if you are not familiar with the command line than SFTP will do. If you are not sure you can use it with your hoster, shoot them an email. Imagewize is running on a Dreamhost VPS and SSH, SFTP and much much more is not an issue. See more info here.
Server Patches
Make sure the server software is up tot date too and that the latest security patches have been applied.
SSL
Besides the fact that Google will love you more it is good to encrypt traffic from and to your site. This can be done using SSL and guarantees better privacy and make logging in and adding posts way more secure than doing it all in the open and sending username and password data across the web.
WordPress Security Tip III Brute Force Preventive Measures
Username and Password
To make brute force hacking as well as manual login hacking harder do not use admin for the administrator, but a unique user name and use a password that is hard to guess. I recommend KeePassX for storing and generating strong passswords. It is a great tool that runs on OSX (Mac), Windows and Linux and is Open Source.
.Htaccess Authentication for Login
To avoid brute force attacks there is a a solution that will allow you to avoid most if not all of it and that is old fashioned .htaccess authentication – on Apache HTTPD Servers. In your WordPress Document Root add the following to your .htaccess file:
ErrorDocument 401 default AuthType Basic AuthName "Enter login two times and then regular password" AuthUserFile /home/user/domain.com/.htpasswd Require valid-user
This will force the user to enter a password based on the .htpasswd. You will have to adjust the file path of course to make this work. To create a .htpasswd file without using the commandline use this site for example. Or do do it from the commandline using:
htpasswd -c /path/to/file/.htpasswd username
The username is a username of your choice and the password can be added after the prompt when asked for.
NB The 401 ErrorDocument has been added to avoid possible redirect loops. You can read more about password protecting your site in this WP Beginner Blog post.
NBB Full path to .htpasswd is needed otherwise you wind up getting a server 500 error
In my experience this brute force prevention works better than two factor authentication as I had some sites where brute force logins even happened using a two factor authentication plugin like Google Authenticator.
Protect .htaccess
To make sure that the file you use to load most of these security tweaks add this to the main .htaccess or the server apache config file:
<files ~ "^.*\.([Hh][Tt][Aa])"> order allow,deny deny from all satisfy all </files>
This will disallow any access or changing of .htaccess (files starting with .hta) . So make sure there are no plugins that need access like W3 Cache or others. I personally do not use this tweak.
WordPress Security Tip IV – Cross Site Contamination Measures
Make sure your files are CHMOD 644 and your directories or folders 755. This is secure for most server setups running CGI or FastCGI. If you are not sure about this ask your hoster and also read WordPress on file and folder permissions here. Just make sure nothing ever is 777 as it will open the gates to hell. To do it from the commandline you can use:
find . -type f -exec chmod 644 {} ';'
find . -type d -exec chmod 755 {} ';'
Another way is running a PHP script. Create one and add the following
exec ("find /path/to/folder -type d -exec chmod 0750 {} +");
exec ("find /path/to/folder -type f -exec chmod 0644 {} +");Or use the script I added as a gist here. And finally, you can also always use an FTP program like my favorite open source program Filezilla. Sample found here, but can be found anywhere and created by anyone with PHP knowledge and somem *Nix knowledge. Some hosters might block exec commands though. In that case contact them.
If you run many client and or test sites remove old test sites you no longer need. You might forget about them and get those hacked in the process!
WordPress Security Tip V – WordFence for File Monitoring and Site Scanning
WordFence is a great plugin that can help you in many ways. It does automatic scans for you to check your files for malicious code, it blocks brute force attacks on your website, it checks your site on blacklists such as the one maintainted by Google, it can compare your core files and or repo plugins to the ones in the repo to make sure nothing is off.
Truly a great plugin that has helped me a lot lately. I also subscribed to their newslettter to keep track of zero day vulnerabilites and or other issues such as server weaknessse.
WordPress Security Tip VI PHP Execution Blocks and Disallows
To make sure hackers will not be able to execute all kinds of crazy script in the includes, uploads or admin folder there is a .htaccess file with a snippet you could add. You just need to make sure it does not blocks execution of files that you truly need.
Here is a snippet WP Beginner created:
AuthName "Admins Only" AuthUserFile /home/yourdirectory/.htpasswds/public_html/wp-admin/passwd AuthGroupFile /dev/null AuthType basic require user putyourusernamehere Order allow,deny Allow from all Satisfy any
Again the same principle as with the login file. You disallow direct wp-admin access unless a password and username is provided.
For the wp-includes and uploads you can directly blocks usage of PHP using:
<Files *.php> deny from all </Files>
WP Config Protection
To make sure wp-config.php is not accessible with ease you can use
<files wp-config.php> order allow,deny deny from all </files>
WordPress Security Tip VII – WordPress Tweaks
There are also a few general WordPress tweaks to apply to secure your WordPress setup some more.
Remove Version Number
Hide or remove the about.php and readme. These two files give away essential information about your site and should not be given away that easily. Edit. No longer really useful as there are too many tools to figure it out.
Security Keys
Add the authentication keys to wp-config.php. This is to secure your cookies better using better encryption. You can generate them on the fly here. Here is an example you should not use is it is rather public now:
define('AUTH_KEY', 'Af|o3G&Bk)3C0+CDB`BTi$-_0;}UjZF{p/7;Mo<zquxV*6;bjudw{HX]:zUujuo['); define('SECURE_AUTH_KEY', '.+x65|n|y;p^j,tb1u|{hjLsSb^S cC7cV@>R5..b*}KqWT2tM!qWn$$+{m*T+jt');
define('LOGGED_IN_KEY', '+|?*RTUv7ls#Z}wC?g>J~56CDiW.1]^yty<s9Ukk~;E#bD&iYs1DgmFZowNP5vrr');
define('NONCE_KEY', 'f6byp~ijOif2|+mE0i!,9qEo<T6__cO0uhMJG#0Jzp3_Abjo-%/+N,H!r856){>;');
define('AUTH_SALT', '|EXau1>Ihx)+Y.0AO^MI^1YRNk+<9FqeOp0xcwrbCzX]j>*Ekl`dy:i(Qa~+m6Z+');
define('SECURE_AUTH_SALT', '}ZIRZgFq/v|C&umuUw]!{f{e|.HpG6VFIQ?91nvYZ!jbXIFr8p~NM|cu:RqAi]&+');
define('LOGGED_IN_SALT', '=@oSGkr2wp*aZB~cx)eYu+|BV|ugbG&|`|.C-b-sOQq~T:_[Xke:|)KY?S<;dj9S');
define('NONCE_SALT', 'Mny:F sB[}J!<hG-y:(ti0-!AiLz*6DvxO+r0&N^vohFK@m5<04KCwd<9M)4/;?|');
No to wp_ Prefix
Do not use the wp_ prefix for the database. Use another more unique prefix. This makes possible MySQL Injections slightly harder. There is a plugin Change DB Prefix that does this for you. You can also do it using PHPMyAdmin.
Or to make sure it is done on installation change the prefix in wp-config.php before you start the installation.Look for this bit of code and change the table prefix accordingly:
/** * WordPress Database Table prefix. * * You can have multiple installations in one database if you give each a unique * prefix. Only numbers, letters, and underscores please! */ $table_prefix = 'wp_';
See more options and details on DigWP here. Either way, please backup your site first!
No longer really valid as latest scripts used to hack sites can easily figure out the prefix used.
Disable File Editing
Disabling file editing using the WordPress file editor and thereby making it impossible to edit files from the Dashboard is another extra possible way to secure your site. It will make it harder to change theme files. Add this snippet to wp-config.php:
Define('DISALLOW_FILE_EDIT', true);
WordPress Security Tip VIII – WP Scan
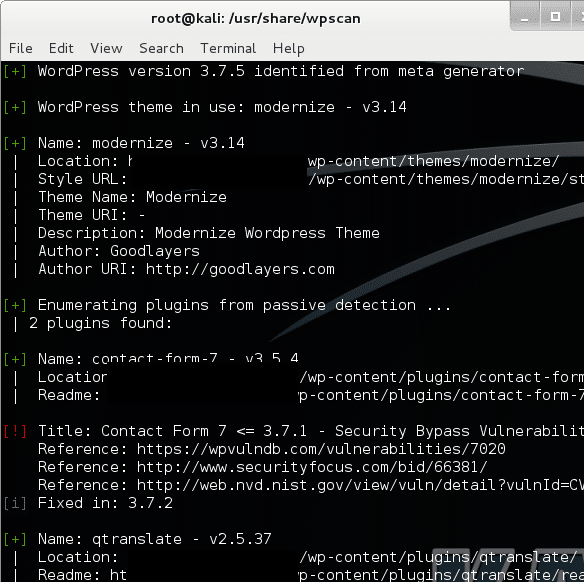
There is a free Ruby based tool called WP Scan. It is a command line based tool that allows you to scan WordPress sites for vulnerabilities. This tool is used by both whitehat and blackhat hackers.
Installing is easy. Either download and unzip or git clone the repo. You do need Ruby and a *Nix system to run it on as Windows is not supported. Do use it ethically to help yourself, your friends or clients. Example of a command for doing a passive scan:
ruby ./wpscan.rb --url http://domain.com
WordPress Security Tip IX – Sucuri Check
Sucuri are really famous in WordPress land in the field of security. They provide a free scanning tool to check your site for possible malware and or spam and offer their services to help you clean up if need be. They also check your site on multiple blacklists with Google being the main one to make sure you are not blacklisted if you have been infected. Sometimes you still have time to clean up before that happens and that is great. Sometimes you are out of luck and then you need to clean up and ask for Google to check your site again to get removed from the aweful blacklist.
here their promo video
WordPress Security Tip X – Hire me!
Yes people, to get help to clean up your site, to maintain your site you need skills and or time and I know many do not have it so leave a message to discuss what I can do for your business here!
Featured Image: Daniel Rehn


